Tech
Conversational AI and Deepfakes: The Future of Human-Computer Interaction
Published
1 year agoon
By
admin
Deepfakes and conversational AI, are the two areas that are fast developing and it is altering in the manner where people engage with computers. Conversational AI, also known as chatbots, enables consumers to connect along the computers with the help of natural language. Deepfakes, conversely, make use of ML processes to create realistic acoustic, video, and pictures which might be used to imitate humanoid behavior. Let us get a thorough knowledge of all of such terms.
Technologies that comprehend, react to and get knowledge via interactions with clientele are what the benefits are given by this tool. Using NLP, also voice acknowledgment, among additional technologies, chatbots and automated assistants can assist customers. in resolving problems in a small amount of time over the phone, on the web page, or via messaging approaches.
Although they are not alike, both are connected. A larger phrase that describes technologies that enable robots to read, understand, and reply to human linguistics refers to something that has been done by conversing with people and Chatbots are part of this tool.
Conversational AI Development is a fast-expanding science that has numerous potential apps in a diversity of areas. It includes the medical profession, businesses, and e-commerce, among others. Conversely, it is important to make certain that such systems are made in a reasonable and principled manner, with a particular emphasis on assuring that they are accountable and see-through.
What is Deepfake?
Today AI might be applied to make deepfake, which can take the procedure and methods of movies, pictures, or sounds which is sufficiently realistic and further could trick viewers into thinking where people are seeing or listening to something that is never genuine. To convey the convincingly fraudulent features of such, they are built utilizing advanced deep learning systems that combine these actions of deep learning as “fake.”
The term Deepfake is a mixture of these two “deep” and “deep knowledge”, which refers to a complicated part of ML that creates the use of AI neural systems. The main aim of this is to expand the competence of computer programs to extract delicate characteristics or micro-data via data having amazing accuracy. Because the “fake” component is such that the idea is that all the information must seem to be genuine.
There is no doubt about the chances and benefits. In the distant future, we might anticipate the expansion of these psychologically complex AI data analysis systems. In the procedure of declassification, technologies that are applied in secret projects will eventually make their mode in the public. The usage of these technologies violates people’s rights to privacy, those who build technology and those who set legislation would be required to address the issues of privacy. Nevertheless, we can imagine a future where artificial intelligence would boost the efficacy of enterprises and individuals equally, offering the right privacy-protecting expertise and strategies in the correct place.
Why is Human-Computer Interaction (HCI) significant to the advancement of expertise?

Developers and engineers prioritize the function of a solution and aim to deliver an engineering-based resolution to an existing issue. It mainly analyzes the dynamics of human-computer interaction and the degree to which humans may engage with computers. This interdisciplinary area takes into consideration a wide range of subjects, including computer science, behavioral studies, cognitive research, ergonomics in psychology, and the ideas of design. A few instances of how human-computer interaction has obstructed the tech field are below:
1.A Voice-guided program
Voice-guided programs are becoming an increasingly normal component of our day-to-day communications, regardless of whether you communicate with Cortana. The customers of these voice assistants can simply ask for what they want, eliminating the need for them to worry about making a mistake or interrupting vital work to research an issue.
The purpose of such interactions is to make the process of getting knowledge as easy and simple as possible like you were having a conversation with a close friend instead. Throughout HCI experiments, designers got significant insight into the distinctions between how humans communicate with one another and the way they communicate with this tech tool.
2.Software that monitors the eyes
For individuals who are afflicted by infirmities such as complete paralysis, using a keyboard to press out guidelines will not be feasible. However, as consequent developments in eye-track software, hundreds of individuals can now merely see a screen and make use of specialized software to execute orders.
The rise in the knowledge of handlers for persons with incapacities wouldn’t be in one place now if (HCI) did not repeatedly appraise ways to make technology more accessible to a wider diversity of people.
3.Speech Acknowledgement Expertise
For the aim of enabling customers to speak with their autos, gadgets, and additional items, it is used by Google Assistant, Amazon’s Alexa, and lots more tools. Both tools work in an organized to improve the relationships between humans and machinery and to offer devices the quiet accurate clarification of user instructions and questions.
4.Health Trackers
(HCI) have applied the authority of measuring your fitness openly towards the grip of the user, as opposed to the traditional method of checking health via a medical practitioner. The convenience of one ca able monitor your well-being through ease of your own home is available by the variability of wearing fitness trackers and smartphone applications that compute your sleep cycle. With the support of HCI, the procedure of monitoring our fitness has become more interesting and interactive. So to uphold our motivation and sense of accountability, we may participate in virtual communities, compete with our friends, collect badges, and create objectives.
5.VR
VR is redefining the kind of Human-Computer Interaction that is feasible for everyone from video gamers to designers. Additionally, virtual reality has made training simulations more effective and realistic, which has enabled experts in industries such as aviation and medicine to practice complicated procedures and circumstances in a situation that is safe and under control. It has the probable to transform the entertainment business, also it could transform people in other sectors to engage with the activities they do on a day-to-day basis with their professions.
Importance of HCI to the expansion of AI world
The findings of investigations directed by firms like Adobe, Microsoft Azure, as well as Facebook are often translated into technical advances that underwrite the change of graphical user interfaces which are instinctive and useable all over an extensive range of sectors. Voice is merely the formation of the development of user interfaces, that will continue to progress.
Exciting new expansions in ML, VR, and AI are at the skyline. The connection that occurs among people and processes is becoming progressively more robust, and it will eventually include all of our minds in addition to our vision, hearing, as well as touch.
We are living in an era in which science fiction has grown into a reality, and our connection with expertise is experiencing the thoughtful transformation that is developing more conceivable where we can artificially produce features that we previously believed were uniquely humanoid.
Deepfakes: A Double-Edged Sword

Just like any additional tool, the effect of deepfake expertise is contingent on how they are applied Deepfakes, can get applications that are open and also thought-provoking. They can modify the entertainment business by offering filmmakers the capability to resuscitate performers who have passed away or to produce realistic computer-generated characters at a lower cost. In addition, they have the potential to be an effective tool for parody or mocking, so giving comic and creative expression a fresh lease of life. In addition to tools, there is an immediate requirement for regulation from not just government organizations but also technological businesses. Collaborations between these businesses must be formed so to bring cross-platform tools for detection to combat deepfake films.
The Moral Implications of Deepfakes in HCI
Despite the truth that deepfakes have attracted a lot of interest in the potential they offer in the imaginative as well as entertainment sectors, several concerns have been raised about them. Concerns have been raised about the possibility for deepfakes to be misused in the dissemination of untruthful info, impersonation, or also extortion because of the simplicity with which they could be created and distributed now. In addition, the usage of deepfakes in the background of HCI is likely to result in the exponential growth of propaganda, management, and disinformation.
To address such problems, researchers and expert firms are actively functioning on the progress of detection approaches and remedies that could identify deepfakes and lessen their effects. These include examining discrepancies in facial expressions, eye movements, or aural clues that may suggest information that has been edited.
The Responsibility of Regulations and Policies
There have been demands for governments to swiftly adjust to the variations that AI is presently giving as well as the potentially transformational changes that will soon have advantages and drawbacks of AI.
Due to the usage of social media, flaws can spread substantially more quickly without being subjected to any checks. They can become viral in just a few seconds of being uploaded. A collaborative effort between policymakers and specialists in the area is required to properly govern conversational artificial intelligence and deepfakes. These specialists include AI researchers, ethical philosophers, lawyers, and investors from a variety of businesses. That rules are informed, thorough, and flexible to the fast-expanding atmosphere of HCI is ensured by this multi-disciplinary strategy, which guarantees that legislation is well-informed.
You may like

Microsoft’s Windows is the cornerstone of personal computing – a platform billions rely on daily. In October 2021, Windows 11 debuted as the boldest Windows upgrade in years, boasting a modern interface, tighter hardware requirements, and features that reimagine productivity, gaming, and security.
This comprehensive guide—reflecting insights in “https://seguridadinformaticahoy.com/todo-sobre-windows-11”—dives into every facet of Windows 11: from its core design and feature set to performance improvements, tips, and potential caveats. Whether you’re a home user, gamer, or enterprise IT pro, you’ll gain a deep understanding of what Windows 11 truly delivers.
What’s New in Windows 11
Windows 11 is more than a minor facelift—it’s built on fresh aesthetics, AI elements, and next-gen hardware integration. Here’s what stands out:
-
Centered Start Menu & Taskbar: A macOS-inspired design with revamped icons and a centered layout that balances minimalism and efficiency.
-
Widgets: Reimagined widgets panel offering news, calendar, weather, and productivity insights at a glance.
-
Snap Layouts & Groups: Effortless window arrangement and group recall—great for multitasking and workflows.
-
Microsoft Teams Integration: A built-in Teams Chat accessible via the Taskbar.
-
Android App Support: Users can install Android apps via the Amazon Appstore (currently via beta).
-
Gaming Features: Auto HDR, DirectStorage, and optimized graphics performance.
-
Improved Windowing: Focused on sleek transitions, rounded corners, and taskbar enhancements.
All these updates are fully explained in “https://seguridadinformaticahoy.com/todo-sobre-windows-11,” which highlights Microsoft’s goal: reinvent usability while aligning with modern hardware trends.
System Requirements & Installation Guide
Minimum Requirements
To run Windows 11, your system must meet:
-
CPU: 1 GHz or faster, 2+ cores, 64-bit, on approved list
-
RAM: 4 GB
-
Storage: 64 GB
-
Firmware: UEFI, Secure Boot capability
-
TPM: Trusted Platform Module (TPM 2.0)
-
Display: 9” or larger, HD (720p), 8 bits/channel
-
Graphics: DirectX 12 / WDDM 2.x compatible
-
Internet: Microsoft Account + internet required for Home editions
TPM 2.0 proves essential and has sparked controversy with legacy machines being left out. But it’s a cornerstone for upgraded security.
How to Check Compatibility
-
PC Health Check App: Official tool from Microsoft.
-
Third-Party Tools: Utilities like WhyNotWin11 offer breakdowns.
-
BIOS Settings: Enable TPM, Secure Boot, virtualization.
Upgrade vs. Clean Install
-
In-Place Upgrade: Keeps your files/settings; easiest route for current Windows 10 users.
-
Clean Install: Fresh start; ideal for reclaimed SSDs or wiping malware. Use the official Media Creation Tool or ISO.
Step-by-Step Clean Install
-
Backup files with OneDrive, external drive, or clone tools.
-
Download Media Creation Tool from Microsoft.
-
Create Bootable USB (8 GB min).
-
Enable Secure Boot & TPM 2.0 in UEFI.
-
Boot from USB and install.
-
Sign in with Microsoft Account.
-
Personalize & activate updates/apps.
Don’t skip updates—they often fix teething issues for new adopters.
Redesigned Interface and User Experience
Aesthetic Refresh
Windows 11 introduces:
-
Centered Start & Taskbar with floating windows and rounded corners.
-
New system icons for modern consistency.
-
Transparent Acrylic taskbar, enhancing design depth.
-
Light/Dark Themes: Sync across elements and support dynamic desktop changes.
Start Menu & Search
-
Simplified layout: Pinned apps show front-and-center; recent files dynamically appear.
-
Universal Search integrates local files, apps, and web results.
Snap Layouts, Groups & Desktops
Hover over maximize to access Snap Layouts:
-
Choose layout templates or create your own multi-window setups.
-
Snap Groups let you toggle full multi-app workflows.
-
Virtual Desktops are now customizable with distinct wallpapers.
Widgets Panel
-
Find widgets with Taskbar toggle; personalize news, tasks, weather, and stock info.
-
Built-in Widgets API allows third-party extension over time.
Taskbar & Quick Settings
-
Unified pull-downs for Wi-Fi, volume, battery, and alerts.
-
Notifications appear grouped with an option to clear all in one go.
Productivity Features & Workflows
Microsoft Teams Chat
Integrated in Taskbar:
-
One-click start for personal chat, calls, or screen sharing.
-
Individual chat flow, not the full Teams interface—useful for quick communication.
Focus Sessions & Clock/Pomodoro
-
Set timers, link Spotify, and enable Do Not Disturb.
-
Motivation built in—great for structured work bursts.
Content-Aware Snipping & Screen Recording
-
Snipping Tool and Snag It alternatives are now native.
-
Clips from the xbox Game Bar support both gaming and productivity scenarios.
Voice Typing & Windows Dictation
-
Powered by cloud AI: improved accuracy and punctuation.
-
Rich voice commands for tasks like “delete that sentence.”
Context Menus & File Explorer
-
Simplified right-click options; advanced options hidden under “Show more.”
-
New command bar for File Explorer provides clarity and easier navigation.
Gaming on Windows 11
Microsoft’s PC gaming leap with Windows 11 is substantial:
Auto HDR
Adds high-dynamic-range color to DirectX 11+ games automatically, even non-HDR titles.
DirectStorage
Drastically increases data throughput, leading to faster load times on NVMe drives.
Xbox App & Game Pass
Now native to Taskbar, connecting you to online gaming, social, and streaming.
Unified Game Bar
Overlay for real-time FPS, recording, chat, and performance overlays.
Gamers benefit from more responsive gameplay and immersive visuals.
Security Enhancements
Security underpins Windows 11’s design:
TPM 2.0 & Secure Boot
Foundation for hardware-based encryption, key protection, and system integrity.
Windows Hello & Modern Authentication
Password-free login: facial recognition, fingerprint, and PIN sign-in.
Enhanced Hardware-Assisted Security
VBS (Virtualization-Based Security) and HVCI (Hypervisor-Enforced Code Integrity) are now enabled by default on capable hardware.
Smart App Control
AI-driven tool allowed only signed and trusted apps—blocks malware, office threats. Initially in preview, expanding via updates.
Microsoft Defender Updates
Security core UI redesigned, faster scans, enhanced phishing and ransomware guardrails.
App Ecosystem & Microsoft Store
Store Revamp
Revitalized UI boosts discoverability, faster load, and rich previews.
Broadened App Support
Win32, UWP, PWAs, and unpackaged store apps all available—more inclusive than before.
Android App Preview
Currently in beta via Amazon Appstore and Windows Subsystem for Android:
-
Install popular apps like TikTok, Kindle, and Zoom.
-
Performance still maturing, but early feedback is promising.
Progressive Web Apps (PWAs)
Installable via Edge with offline capabilities—great for frequent web tools.
Tips, Tricks, and Customization
Maximize your Windows 11 experience:
1. Rename Snap Layouts
-
Use
Win + Z, drag windows. -
Customize by dragging and positioning.
2. Create Virtual Desktop Workflows
-
Rename desktops (Work, School, Play).
-
Assign apps to desktops via right-click in Task Manager.
3. Use Focus Sessions
-
Access via Clock app—great for concentration.
-
Adds structure and syncing with Outlook.
4. Enable Smart App Control
-
Found in Settings → Privacy & Security.
5. Turbocharge Performance
-
Use Game Mode, Graphics Performance Preferences, and power plans.
-
Use Task Manager’s “Startup” tab to trim bloatware.
6. Customize the Taskbar
-
Drag items, sliver icons off, and anchor Widgets or Chat.
7. Use New File Explorer Shortcuts
-
Win + Efor Explorer, context switch via shortcut or command bar.
8. Animate with Voice Access
-
Controls like “Open Edge, Scroll down 3 pages, Click link” are fully supported.
9. Harness Whatsapp Web via PWA
-
Install from Edge—gives near-native desktop usability.
10. Tweak Touch & Pen Settings
-
Pen gestures, handwriting recognition, gestures via Settings → Bluetooth & devices.
Common Issues and Troubleshooting
Boot or Blue Screen on Unsupported Hardware
-
TPM 2.0 or Secure Boot issues: check BIOS, or choose Clean Install via ISO.
-
For older CPUs: bypass flag in registry during install—but not recommended for mainstream use.
Battery Drain & Performance Issues
-
AV scans, telemetry, and indexing increase workload.
-
Switch to Balanced or Power saver, disable telemetry via Group Policy.
Broken Audio or Display Drivers
-
Use Intel’s DCH drivers, latest AMD/NVIDIA Game Ready or Studio drivers.
Android App Not Working?
-
Ensure Windows Subsystem for Android is installed and in preview, and enable virtualization.
Taskbar or Widgets Broken
-
Run
sfc /scannow, reinstall stock apps via PowerShell (“Get-AppxPackage…”).
Snap Layout Stuck?
-
Re-enable Snap Assist in Settings → System → Multitasking.
FAQs
Is Windows 11 a free upgrade?
Yes—if you’re on licensed Windows 10 with hardware support, Microsoft offers a free upgrade via Windows Update.
Can I revert to Windows 10?
Yes, within 10 days of upgrade. Settings → System → Recovery → Roll back.
Why do I need TPM 2.0?
It secures keys and system integrity; foundational for modern ransomware resistance.
Are all Windows 10 apps compatible?
Over 99% install and run fine. Only a few low-level tool conflicts—mostly edge cases.
Do I need a Microsoft account?
Home edition requires it. Enterprise/LTSC allows local accounts.
Personalization tied to account access.
Conclusion
Windows 11 stands out not just in design, but in performance, security, and flexibility. Whether for daily tasks, creative workflows, or immersive gaming, its refreshed UI, productivity enhancements, and robust security make it compelling.
From rounded corners and centered Taskbar to Auto HDR and Smart App Control, it brings modern polish across the board. TPM 2.0 and VBS keep your system protected against modern threats. Android app support and progressive web apps broaden your software horizons.
Tech
Top 3 Advanced Persistent Threats and How Businesses Can Stop their Attacks
Published
3 months agoon
April 24, 2025By
admin
Businesses of various sizes and fields are susceptible to advanced persistent threats (APTs). According to the cybersecurity company ANY.RUN, in the first quarter of 2025 the most active phishing groups were Storm1747, TA569, and Storm1575. isn’t limited to, finance, media, and cybersecurity.
To protect the infrastructure of your organization, learn about their tactics and weak spots below.
Storm1747 – detected 16,140 times in January–March 2025
Storm1747 is a cybercriminal group responsible for the Tycoon 2FA phishing kit. It’s known to evade detection systems by using malicious QR codes. Still, such attacks don’t go unnoticed. The adversaries leave traces, and they can be identified.
To retrieve information on them and protect your company, use threat intelligence services. Here’s how to investigate threats in ANY.RUN’s TI Lookup, a constantly updated searchable database of IOCs, IOAs, and IOBs of the most recent attacks:
1.Enter the query
TI Lookup allows you to conduct compound searches. For example, let’s browse its database to look for threats flagged as Storm1747 and involving QR codes by entering this query:
threatName:”storm1747″ AND threatName:”qrcode”
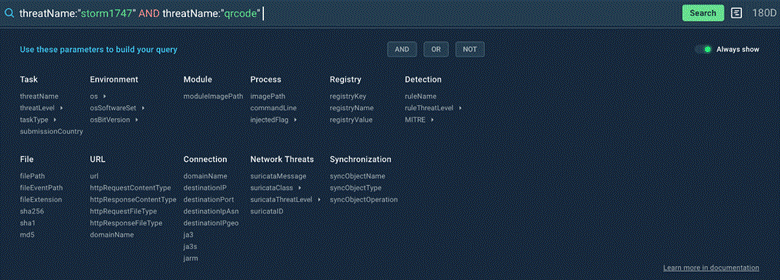
In TI Lookup, you can form compound searches with any of over 40 available parameters
Explore current cyber threats with 50 trial requests in TI Lookup
2.See the results
Now we can see a list of all freshly gathered threat samples that fit our requirements:
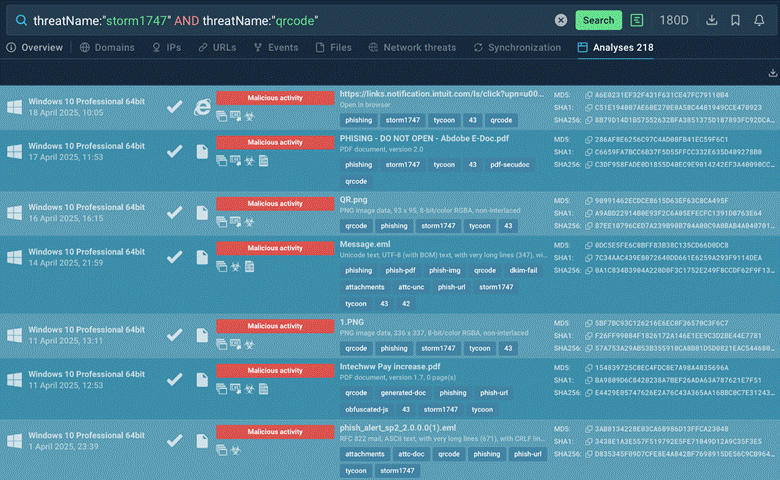
The list of threat samples that fit our query
3.Collect actionable intel to enrich your defense
Each contains an in-depth threat context. By clicking any of the search results, you can continue the analysis in ANY.RUN’s Interactive Sandbox for malware analysis to collect detailed info on each threat and interact with malicious files safely to understand their behavior:
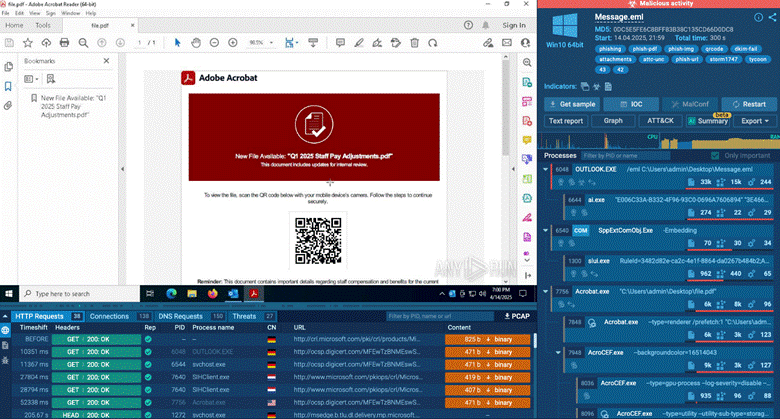
Interact with malware for further analysis in ANY.RUN’s Sandbox
That’s how you can analyze recent attacks, collect their indicators, and take measures to protect your company from upcoming threats associated with them.
TA569 – detected 1,005 times in January–March 2025
TA569 is a threat actor responsible for the SocGholish malware injected into compromised websites via malicious JavaScript.
With this simple search query in TI Lookup, we can find our which domains fell victim to SocGholish:
threatName:”socgholish” AND domainName:””
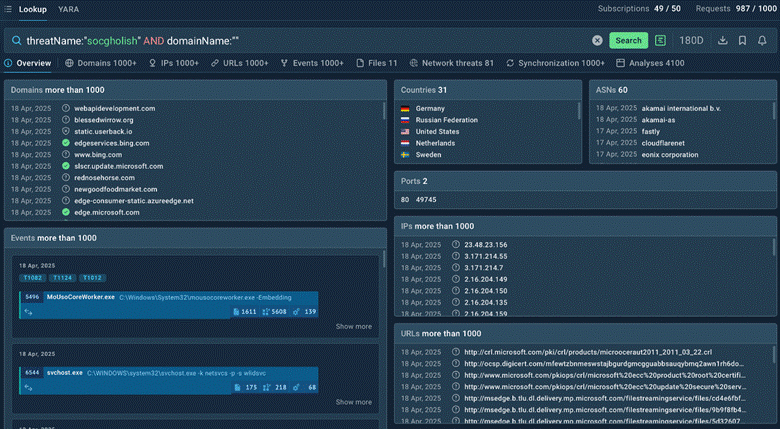
Search results for domains associated with the SocGholish
You can also subscribe to this or any other query via the Search Updates feature to keep track of the threats as they evolve. In this case, information on fresh attacks will appear on your dashboard highlighted in green.
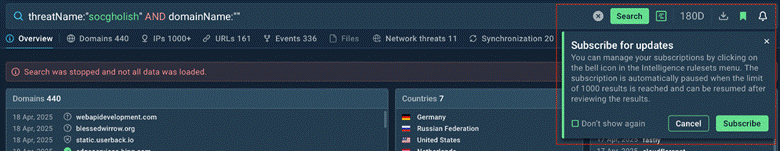
Search Updates in TI Lookup allow you to track evolving threats
Storm1575 – detected 762 times in January–March 2025
TI Lookup allows you to check if an indicator has anything to do with a threat. For instance, you would like to find out whether a website is related to malicious activities. All you have to do is to browse the database for its mentions using a query like that:
domainName:”castirontexas[.]com”
And in a moment’s time, you’ll know that this website is associated with Storm1575, one of the leading recent cyber criminal groups. It’s known to conduct attacks targeting companies globally via the Dadsec platform.
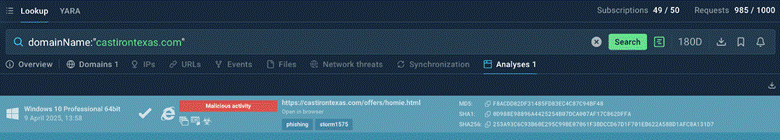
The website we checked is associated with malicious activities
Try TI Lookup to Enrich Alerts and Speed up Incident Response
TI Lookup’s searchable database provides you with the most up-to-date information on the latest cyber threats and enables business and organizations to:
- Detect and identify attacks before they cause damage
- Investigate and browse IOCs, IOAs, and IOBs for more insights on threat actors
- Enhance the efficiency of your security team’s workflow
- Gain access to data that helps take proactive action against cyber threats
Over 500,000 security professionals worldwide, including SOC teams from 15,000 companies, contribute to ANY.RUN’s database, keeping it relevant and abundant.
Tech
How Accurate Pulley Alignment Can Prevent Equipment Failures
Published
3 months agoon
April 22, 2025By
admin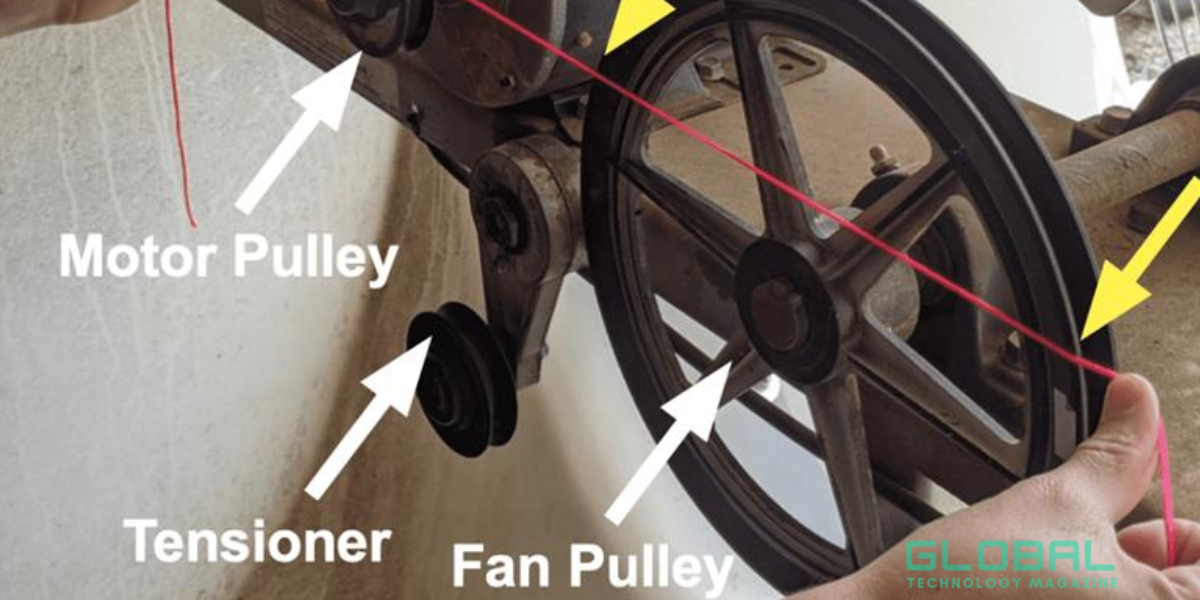
In industrial settings, the smooth operation of machinery is essential for productivity and safety. One often overlooked aspect that can significantly impact machinery performance is pulley alignment. Proper alignment of pulleys ensures that belts run smoothly, reducing wear and tear on equipment components and minimizing the risk of costly breakdowns. In this article, we’ll explore the importance of accurate pulley alignment and how it can prevent equipment failures.
Understanding Pulley Alignment
Pulleys are critical components in various types of machinery, including conveyor systems, pumps, and motors. They transmit power from one rotating shaft to another via belts or chains. When pulleys are misaligned, even slightly, it can lead to a range of problems, including increased friction, excessive vibration, and premature wear on belts and bearings.
Common Causes of Misalignment
Several factors can contribute to pulley misalignment, including:
- Installation Errors: Improper installation of pulleys or shafts can result in misalignment from the start.
- Belt Tension: Inadequate or uneven belt tension can cause pulleys to shift out of alignment over time.
- Shaft Deflection: Shaft deflection due to excessive loads or improper support can lead to misalignment issues.
- Thermal Expansion: Temperature fluctuations within the machinery can cause components to expand or contract, affecting pulley alignment.
Impact of Misalignment on Equipment
Misaligned pulleys can have significant consequences for machinery and production processes, including:
- Increased Wear and Tear: Misalignment causes excessive friction, leading to accelerated wear on belts, bearings, and other components.
- Reduced Efficiency: Machinery operates less efficiently when pulleys are misaligned, resulting in higher energy consumption and reduced productivity.
- Vibration and Noise: Misalignment often results in excessive vibration and noise, which can be disruptive and potentially harmful to equipment and personnel.
Preventive Measures
Preventing pulley misalignment is key to maintaining equipment reliability and prolonging service life. Here are some preventive measures to consider:
- Regular Inspection: Conduct routine inspections of pulley alignment using precision tools such as a laser alignment tool. Identify and correct misalignment issues promptly.
- Proper Installation: Ensure that pulleys and shafts are installed correctly according to manufacturer guidelines to minimize the risk of misalignment from the outset.
- Belt Tensioning: Maintain proper belt tension to prevent slippage and minimize the likelihood of pulley misalignment.
- Temperature Monitoring: Monitor temperature fluctuations within the machinery and take measures to minimize thermal expansion effects on pulley alignment.
Importance of Laser Alignment Tools
Laser alignment tools are invaluable for achieving precise pulley alignment. These advanced devices use laser technology to measure and adjust the position of pulleys with unparalleled accuracy. By providing real-time feedback and visual guidance, laser alignment tools enable operators to achieve optimal alignment quickly and efficiently.
Conclusion
In conclusion, accurate pulley alignment is crucial for preventing equipment failures and ensuring the smooth operation of industrial machinery. By addressing misalignment issues proactively and utilizing advanced tools such as laser alignment tools, manufacturers can minimize downtime, reduce maintenance costs, and enhance overall productivity. Investing in proper pulley alignment practices is a wise decision that pays dividends in the form of improved equipment reliability and performance.
Remember, maintaining optimal pulley alignment is not just a matter of efficiency—it’s a fundamental aspect of ensuring the safety and longevity of industrial equipment.

The Ultimate Guide to the Best Android Strategy Games in 2025: What to Play and Why

What Are the Most Effective Digital Marketing Strategies?

Everything You Need to Know About Windows 11

The Best E commerce Platforms for Small Businesses in 2025

How to Start Coding from Zero Level with No Prior Experience

Why Great Output Doesn’t Always Mean Great Performance

Top 3 Advanced Persistent Threats and How Businesses Can Stop their Attacks

14 Actionable Tips to Improve Your Manufacturing Business

10 Tips for Optimizing Images for SEO

10 Most Profitable Businesses in India
Trending
-
 Miscellaneous3 years ago
Miscellaneous3 years agoSubnautica Below Zero Map – Know About Complete World Map and Coordinates 2021
-

 Mobile2 years ago
Mobile2 years agoVivo Company Belongs to Which Country? Vivo Made in Which Country? Is Vivo Chinese Company?
-

 Gaming2 years ago
Gaming2 years agoWhen Did the PS4 Come Out
-

 Gaming3 years ago
Gaming3 years agoWhy F95 Zone is the Leading Gaming Community?

